Target name : Toppo:1
IP address: 10.10.10.2
Level: Easy
Download url : https://www.vulnhub.com/entry/toppo-1,245
First of all, as always we do, we launch netdiscover[1] to find the IP address of the target on the network.
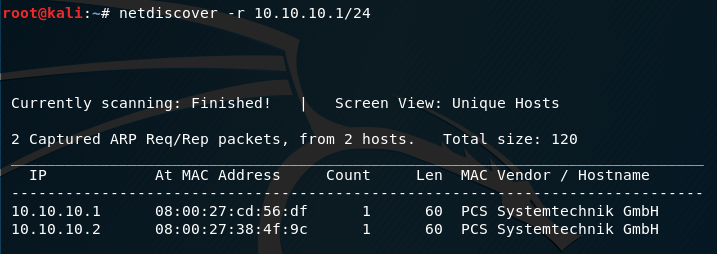
in this case the target’s IP address is 10.10.10.2.
[1] netdiscover small documentation : https://kalilinuxtutorials.com/netdiscover-scan-live-hosts-network/
Now that we have the IP address of the system, we can perform a simple port scan on it to check which doors could be unlocked on this little house.

In order to do it, a nice start would probably be starting nikto[1] on the port 80 while poking a the website manually. Of course in a real situation checking some easy creds on the ssh service would be nice but hey its a CTF, lets be honest, that would be boring af…
At first, there’s nothing interesting. So let’s check our nikto result which is much cooler.

As we can see here, nikto found two “interesting” folder. /admin & /mail
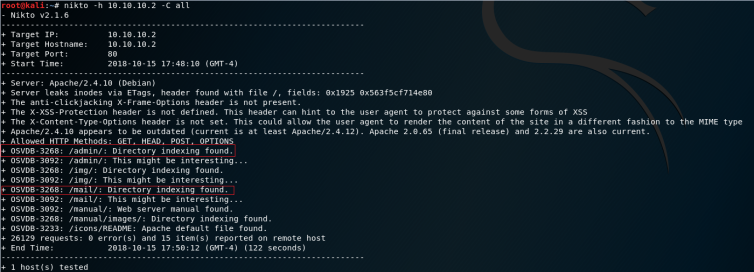
[1] nikto documentation : https://cirt.net/nikto2-docs/
By browsing the /admin folder, we find a pretty sweet note that stupid system owner.

Thanks for the info…

So from that info we learn two things. the system owner’s name is ted and his password is 12345ted123.
So what about try these creds on the ssh service :).
username: ted
password: 12345ted123
At our surprise, the creds works. Now the only question remaining is.. how can we get root ??

As we always do on a freshly owned system (in a CTF situation of course), We copy the linenum.sh[1] script from github in order to make an executable script on the system with the help of vi[2].

The output of LinEnum is pretty verbose but the line that we are interested in is that one.

By searching a little bit on google, we can find a pretty nice blog post about exploiting the awk command to execute a shell[3]. So if we combine these two informations we got the expected result, which is getting root on the system and GTFO.

[1] LinEnum source code : https://raw.githubusercontent.com/rebootuser/LinEnum/master/LinEnum.sh
[2] small vi documentation: https://www.ibm.com/developerworks/library/l-lpic1-103-8/index.html
[3] awk command exploit: https://www.andreafortuna.org/cybersecurity/exploiting-sudo-for-linux-privilege-escalation/
凄いいいいい!
LikeLike